Internet is an environment full of threats – a truth well known to all. The number of cyber-attacks is increasing every year, with the media reporting on audacious stealing of data or hacking into bank accounts every few months. Currently, a significant part of our lives takes place online, so it is virtually impossible to avoid danger. This is evident in business matters as well – it is difficult to run a company without online activity. Therefore, the most important element is caution and constant care for safety. It is necessary to use proper security measures and follow procedures, especially when using business equipment carrying sensitive data.
What puts a company at risk?
It may initially seem to us that the main problem is the security measures and software used. However, it may lie in a completely different place. Machines and applications always operate in a pre-programmed way, carrying out human commands. They are not spontaneous, do not take shortcuts, and always follow certain procedures.
Who is therefore the weakest link in this system? Not sure? Look in the mirror! The factor that poses the greatest risk is always a person. It could be either an IT specialist who administers the company’s system, or a user who does not follow the guidelines. In the following text we will discuss these very situations.
How to reduce the risk of online and offline threats?
Since the human factor is the reason for most security breaches of IT infrastructure, the key to avoiding problems will be systematic awareness raising. Thus, it is necessary to conduct cyclical trainings to ensure consolidation of security principles.
Employees who have, in theory, knowledge of the dangers coming from the Internet often ignore it. Some people think that the probability of an attack caused by their irresponsibility is actually so small that it is unrealistic. Such an attitude very often becomes the first step to disaster.
Employees should be made aware that online scammers are not mythical creatures who attack one random user among millions. Instead, their attacks are most often massive, and even if they take only a specific company as their target, they will most likely attack many employees. Bear in mind, too, that behind most attacks are not just humans, but malware with a mass-scale focus. Ignorant behavior on the Internet is equivalent to leaving the door to your house wide open hoping that a thief doesn’t notice it.
Phishing attacks
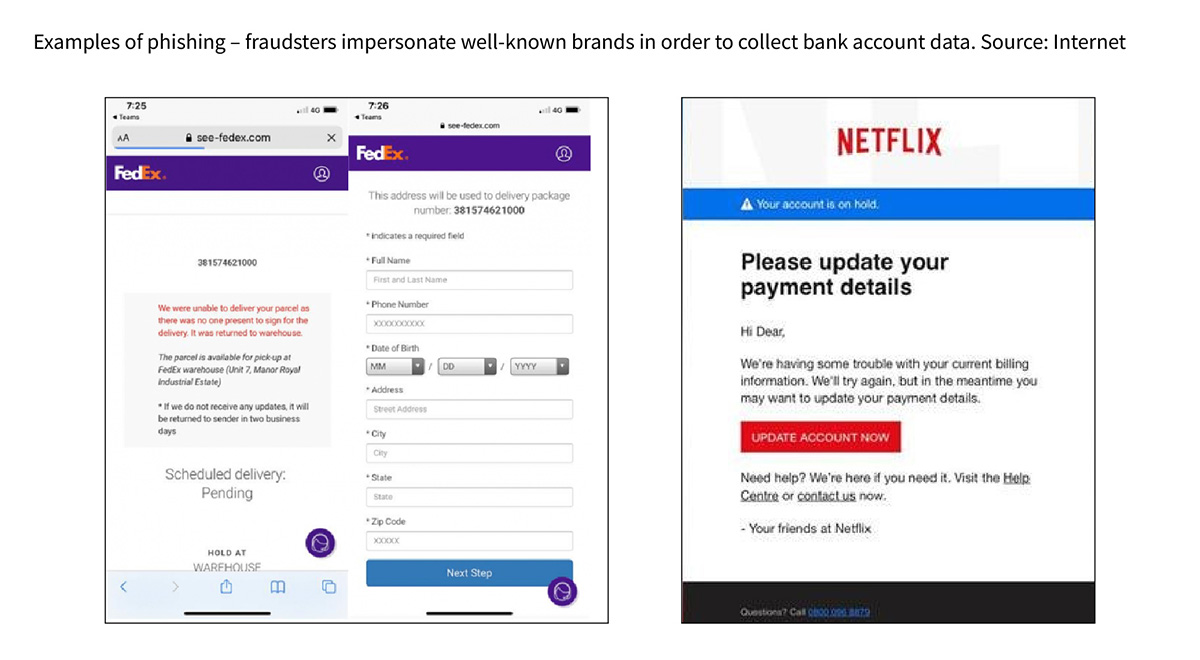
Nowadays, phishing attacks are the most popular. They are aimed at phishing for sensitive information such as login credentials or credit card numbers.
So how does this kind of attack look like? Quite inconspicuously. An employee usually gets a message that seems deceptively similar to ordinary office correspondence. The scammer may claim to be a client, a co-worker or an external entity. Any reference provided in the email would look like a real and harmless links that are leading to a seemingly trusted site, such as a bank’s website. Once you log on to the fake site, your login information will fall into the wrong hands.
Other reasons for password leaks
The introduction of procedures for the creation and secure storage of passwords is an issue that has a huge impact on the security of the company.
When workers create their personal access data, for example, for a company’s IT system, e-mail or Google account, they should pay special attention to making their password complex and hard to guess. It is essential to use both uppercase and lowercase letters, numbers and special symbols. Also extremely important is the number of characters used – the more, the better since the harder and more time-consuming the process of cracking the password will become.
All of these factors are of great importance. If we wanted to create a password that consists of just one lowercase letter, we would have only 26 options available. It would therefore be very easy to crack. Each additional letter multiplies the number of combinations by 26. If we add special characters and capital letters, the number of options becomes much larger.
According to Forsal.pl, it would take only 1 day for a computer to crack a password consisting of 11 letters. If the combination includes uppercase and lowercase letters and special characters, the computer may need up to 43 years to crack it .
Regular change of passwords and avoiding their repetition in different places is important too. They should be not saved in the browser either, because in case of data leakage, all stored passwords will be revealed.
How to secure your password?
Even the best thought-out, difficult password will not protect our data if it falls into the hands of an unauthorized person. Thus, the way it is stored is very important. Listing the passwords in a notebook saved on the desktop and titled “passwords to secret company files” is not the best idea. Writing it down on a piece of paper or in a notebook that permanently lays on our desk or travels with us in a bag or backpack is also a potential danger.
Certainly, it is impossible to remember all your passwords, which is why the best solution would be to save them in an encrypted database. You can find many free programs on the Internet that allow you to create such a database. An excellent example is, among others, the Keepass program. A Microsoft Word document protected by a password will also work well for such a database.
We should also remember that providing employees with tools is not enough, and frequent reminders about the principles of secure password storage are also necessary. In some cases, an audit on the passwords among employees can be considered. The very information that such measures are planned can bring desirable results.

Sending company files to the public cloud
Password leakage is not the only threat to a company. Also project-related files or confidential data owned by the company can fall into the hands of unauthorized persons. Work computers usually have locked USB ports, so it can be a problem to transfer files, especially larger ones, to another co-worker. In such situations, many of the employees places the files in the public cloud.
However, this is a serious mistake that risks data leakage!
The public cloud is very different from that offered by a Data Center. In the public cloud, the virtual space is not so carefully protected, and files can be stored in any place on earth, not equipped with specialized security. In other words, this is a service on a completely different, lower level, dedicated more to individuals who do not need to worry about the security of valuable data. Putting confidential files in a public cloud is asking for trouble, e.i. data leakage.
It is worth discussing such a situation with your supervisor and determining a secure form of transferring the data, for example, by simply copying it to a flash drive by someone authorized to manage USB ports on the company’s computers.
Remote work
In carrying out our duties remotely, we often abuse the trust that our superiors have placed in us. As soon as we notice how comfortable we feel on the couch, we stop working at our previously prepared desk. Unfortunately, such an approach comes with certain risk. If the work is carried out in an inappropriate place and the laptop rests, for example, on our knees or on the kitchen counter, it can easily fall, get flooded or be damaged in any other way.
Working in a place that is not designed for it carries other dangers as well. Especially if it is performed outside of the house. Indeed, such conditions make it possible for an unauthorized person to overhear our confidential business conversation or see the data displayed on our computer or phone screen.
When working remotely, we should also keep in mind that not every network will be safe for us. Whenever we sit down with our business laptop in a cafe, restaurant or train, for instance, we connect to a public network. Unfortunately, we don’t know who else is using it, which exposes us to potential danger. Similarly the use of a home network, which can seemingly appear safe, is equally risky. Sadly, it is very often protected by a very easy password.
Watch out for malware
Ignorance of security rules can result in infecting your computer with malware that can destroy the contents of your hard drive, cripple your computer or deliver sensitive data to unauthorized parties. It only takes a moment of inattention to go to the wrong website or download a dangerous file. A single warning from an antivirus program that is ignored may be all that separates us from catastrophe.
Malware can take the form of:
- viruses – programs that maliciously affect a computer system,
- ransomware – software that encrypts computer files and forces victims to pay a ransom in exchange for reentry
- scareware – programs that threaten to infect a device and manipulate users into buying applications to solve the problem,
- trojans – programs that steal data and spy on the user,
- adware – programs that display unwanted ads to users.
How do we know that a computer has been infected?
Any “unusual” activity of the computer can be an alarming factor. If we suddenly lose access to files, see brand-new, unfamiliar applications, or are more often presented with unwanted ads, it could be a sign that the device is infected with malware.
What should you do in such a situation? In case a company computer is infected, there is no time to waste. Every minute of delay can increase the losses the company will suffer. This is precisely why it is wise to adopt the following rule: if we have any doubts, let’s report the problem to the IT administrator. It is better to raise the alarm unnecessarily than to trivialize a serious problem.
Company security is helpful, but not perfect
If we assume that IT infrastructure security is like a seat belt, then making sure that employees follow procedures is the equivalent of driving safely. In order to avoid unpleasant consequences, we should behave responsibly, even if we are convinced that the belts will save our lives.
Therefore, both issues are worth taking care of. Looking to protect IT systems from intrusion by unauthorized persons and corporate data from theft or destruction, it is best to use the help of a specialized external entity.
It is necessary to introduce clear rules and remember to follow them. Blocking your computer every time you walk away is crucial. This may seem trivial, yet it is very important. Data theft happens everywhere, even at workplaces when we sit in a room with only “trusted” people. To secure your computer, a good idea is to provide encryption. For this purpose, we can use programs such as Bitlocker or VeraCrypt.
Moreover, systems and applications used need to be updated on an ongoing basis. Outdated versions of the operating system or software can be more susceptible to viruses or hacking attacks. Updates very often include improvements, providing security seals.
The key to security is comprehensive action
Regular training and reminders to employees of applicable policies cannot be forgotten. Only continuous care for their knowledge and awareness would give them a chance to avoid dangers.
All in all, both taking care of a secure IT infrastructure, e.g. by using Data Center cloud services or opting for IT Outsourcing services, and ensuring proper behavior of employees are of great importance, and therefore be sure to conduct training and provide procedure reminders.
